High availability
Configure two HAProxy Enterprise servers for active/standby clustering
This page applies to:
- HAProxy Enterprise - all versions
Using HAProxy Fusion?
If you’re using HAProxy Fusion, then see the HAProxy Fusion - High availability topic instead.
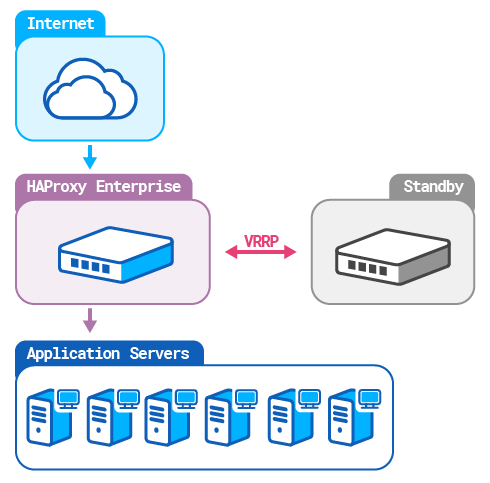
In an active-standby cluster, one HAProxy Enterprise node receives traffic while a second node is put on standby. In case the active node fails, the standby takes over. With HAProxy Enterprise, you configure an active-standby cluster by installing the Virtual Router Redundancy Protocol (VRRP) module.
The HAProxy Enterprise VRRP module assigns a virtual, static IP address to your load balancer node. If the node fails, the IP address will instantly transfer to a backup node, avoiding any break in service. Your router can continue to send traffic to the same IP address for the load balancer, never knowing that there was a failover. The module utilizes a stable version of Keepalived, which implements VRRP.
In this guide, we will set up two load balancers: one active and the other on standby.
Prerequisites Jump to heading
If you have a firewall running on the server, such as firewalld (the default on Red Hat Enterprise Linux) or iptables, then be sure to add an exception for VRRP traffic.
Add an exception to firewalld
To add an exception for VRRP to firewalld:
-
Check if
firewalldis running:nixsudo firewall-cmd --statenixsudo firewall-cmd --stateoutputrunningoutputrunning -
Check which
firewalldzones are active for your network interfaces. Below, our active zone is namedpublic:nixsudo firewall-cmd --get-active-zonesnixsudo firewall-cmd --get-active-zonesoutputpublic interfaces: eth0 eth1outputpublic interfaces: eth0 eth1 -
To ensure that existing runtime rules (those that are in effect) are persisted, save them as permanent before going further:
nixsudo firewall-cmd --runtime-to-permanentnixsudo firewall-cmd --runtime-to-permanentoutputsuccessoutputsuccess -
Add the VRRP protocol to the list of rules. Below, we use the zone named
public:nixsudo firewall-cmd --zone=public --add-protocol=vrrp --permanentsudo firewall-cmd --reloadnixsudo firewall-cmd --zone=public --add-protocol=vrrp --permanentsudo firewall-cmd --reloadoutputsuccessoutputsuccess -
Verify that the protocol has been added. Below, we use the zone named
public:nixsudo firewall-cmd --zone=public --list-all | grep vrrpnixsudo firewall-cmd --zone=public --list-all | grep vrrpprotocols: vrrpprotocols: vrrp -
Make these changes persist:
nixsudo firewall-cmd --runtime-to-permanentnixsudo firewall-cmd --runtime-to-permanentoutputsuccessoutputsuccess -
If you need to revert this change, run these commands:
nixsudo firewall-cmd --zone=public --remove-protocol=vrrp --permanentsudo firewall-cmd --reloadnixsudo firewall-cmd --zone=public --remove-protocol=vrrp --permanentsudo firewall-cmd --reload
Add an exception to iptables
To add an exception for VRRP to iptables:
-
Save a backup of your current
iptablesconfiguration:nixsudo apt install iptables-persistentsudo su -c 'iptables-save > /etc/iptables.backup.rules'nixsudo apt install iptables-persistentsudo su -c 'iptables-save > /etc/iptables.backup.rules' -
Add the VRRP protocol to the list of rules. Below, we specify the interface
eth0:nixsudo iptables -A INPUT -p vrrp -i eth0 -j ACCEPT && sudo iptables -A OUTPUT -p vrrp -j ACCEPTnixsudo iptables -A INPUT -p vrrp -i eth0 -j ACCEPT && sudo iptables -A OUTPUT -p vrrp -j ACCEPT -
Verify that the protocol number 112 (VRRP) has been added:
nixsudo iptables -nvL | grep 112nixsudo iptables -nvL | grep 112output0 0 ACCEPT 112 -- eth0 * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT 112 -- * * 0.0.0.0/0 0.0.0.0/0output0 0 ACCEPT 112 -- eth0 * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT 112 -- * * 0.0.0.0/0 0.0.0.0/0 -
Save the configuration:
nixsudo su -c 'iptables-save > /etc/iptables.vrrp.rules'nixsudo su -c 'iptables-save > /etc/iptables.vrrp.rules' -
If you need to revert this change, run this command:
nixsudo iptables-restore < /etc/iptables.backup.rulesnixsudo iptables-restore < /etc/iptables.backup.rules
Are you using Cisco ACI (Application Centric Infrastructure) in your setup?
A known issue with Cisco ACI occurs after a failover in which traffic continues to go to the load balancer that was formerly the primary. This can happen when the former primary briefly sends out traffic over old connections, causing Cisco ACI to relearn the VIP back to the former primary. Avoid this issue by disabling the IP Data-plane Learning option under the VRF and enabling GARP-based detection. See the Cisco ACI White Paper for more details.
Installation Jump to heading
Follow the steps on your active and backup load balancers.
Active load balancer Jump to heading
On the active load balancer, follow these steps:
-
Install the VRRP module using your system’s package manager:
Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo apt remove hapee-extras-vrrpnixsudo apt remove hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo apt-get install hapee-extras-vrrp22nixsudo apt-get install hapee-extras-vrrp22Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo yum remove hapee-extras-vrrpnixsudo yum remove hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo yum install hapee-extras-vrrp22nixsudo yum install hapee-extras-vrrp22Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo zypper remove hapee-extras-vrrpnixsudo zypper remove hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo zypper install hapee-extras-vrrp22nixsudo zypper install hapee-extras-vrrp22Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo pkg delete hapee-extras-vrrpnixsudo pkg delete hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo pkg install hapee-extras-vrrp22nixsudo pkg install hapee-extras-vrrp22 -
Decide on a unique Virtual Router Identifier (VRID) for the cluster. A VRID can be any number between 1 and 255. It allows the instances in a cluster to share a virtual router and virtual IP address. The VRID must be the same on all instances in a cluster. If there are multiple VRRP clusters in the environment, the VRID must be unique for each cluster.
Don’t use a VRID already in use for another cluster. If the
vrrpservice has been started and enabled, you can list VRIDs already in use by executing the following command:nixsudo tcpdump -vvvenns0 -c 5 -i eth0 vrrp | grep -o "vrid [0-9]*"nixsudo tcpdump -vvvenns0 -c 5 -i eth0 vrrp | grep -o "vrid [0-9]*"outputtext[...]5 packets captured6 packets received by filter0 packets dropped by kernelvrid 161vrid 155outputtext[...]5 packets captured6 packets received by filter0 packets dropped by kernelvrid 161vrid 155In our example configuration, we will use VRID
51. -
Decide on a password for the cluster. The password is a clear-text string for use by all instances in this VRRP cluster. It doesn’t provide security, but it ensures that VRRP instances from other clusters cannot join this cluster due to errors in configuration, such as a duplicate VRID.
-
Edit the file
/etc/hapee-extras/hapee-vrrp.cfg.-
In the
vrrp_instancesection, change theinterfacevalue frometh0to the name of a network interface that receives traffic on the server. This is the same interface that you the bind HAProxy Enterprise’sfrontendto. For example, if traffic reaches the load balancer using interfaceenp0s8. Set this line tointerface enp0s8. -
For the
virtual_router_idvalue, specify the VRID determined previously. -
Change the authentication password in
auth_passto the password determined previously. -
Change the IP address listed in the
virtual_ipaddress_excludedblock to the virtual IP address you’d like to assign to this interface. HAProxy Enterprise will bind to this address to receive traffic. If needed, add more IP addresses here, each on its own line. The new address(es) should fall within the interface’s IP subnet but shouldn’t already be assigned to any server. -
In the
track_interfaceblock, specify the same interface name that is specified in theinterfacefield.
hapee-vrrp.cfgtextvrrp_instance vrrp_1 {interface enp0s8 # Change network interface namestate MASTERvirtual_router_id 51 # VRID unique to this clusterauthentication {auth_type PASSauth_pass 1234 # Text string unique to this cluster}priority 101virtual_ipaddress_excluded {192.168.50.10 # New IP address}track_interface {enp0s8 weight -2 # Change network interface name}track_script {chk_sshdchk_lb}}hapee-vrrp.cfgtextvrrp_instance vrrp_1 {interface enp0s8 # Change network interface namestate MASTERvirtual_router_id 51 # VRID unique to this clusterauthentication {auth_type PASSauth_pass 1234 # Text string unique to this cluster}priority 101virtual_ipaddress_excluded {192.168.50.10 # New IP address}track_interface {enp0s8 weight -2 # Change network interface name}track_script {chk_sshdchk_lb}} -
-
Enable and start the
hapee-extras-vrrpservice:nixsudo systemctl unmask hapee-extras-vrrpsudo systemctl enable hapee-extras-vrrpsudo systemctl start hapee-extras-vrrpnixsudo systemctl unmask hapee-extras-vrrpsudo systemctl enable hapee-extras-vrrpsudo systemctl start hapee-extras-vrrp -
Allow the server to bind to the virtual IP address.
Edit the file
/etc/sysctl.confand add thenet.ipv4.ip_nonlocal_bind=1directive. This directive allows the server to accept connections for IP addresses that aren’t bound to any of its interfaces, enabling the use of a floating, virtual IP.sysctl.confininet.ipv4.ip_nonlocal_bind=1sysctl.confininet.ipv4.ip_nonlocal_bind=1 -
Configure your
bindline in the HAProxy Enterprise configuration to use the virtual IP address.haproxyfrontend myfrontendmode httpbind 192.168.50.10:80default_backend web_servershaproxyfrontend myfrontendmode httpbind 192.168.50.10:80default_backend web_servers -
Reboot the server.
Standby load balancer Jump to heading
On the standby load balancer, follow these steps:
-
Install the VRRP module using your system’s package manager:
Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo apt remove hapee-extras-vrrpnixsudo apt remove hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo apt-get install hapee-extras-vrrp22nixsudo apt-get install hapee-extras-vrrp22Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo yum remove hapee-extras-vrrpnixsudo yum remove hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo yum install hapee-extras-vrrp22nixsudo yum install hapee-extras-vrrp22Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo zypper remove hapee-extras-vrrpnixsudo zypper remove hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo zypper install hapee-extras-vrrp22nixsudo zypper install hapee-extras-vrrp22Remove the
hapee-extras-vrrppackage if you installed it previously:nixsudo pkg delete hapee-extras-vrrpnixsudo pkg delete hapee-extras-vrrpInstall the 2.2 version of VRRP:
nixsudo pkg install hapee-extras-vrrp22nixsudo pkg install hapee-extras-vrrp22 -
Edit the VRRP configuration
/etc/hapee-extras/hapee-vrrp.cfg. It must be exactly the same as the file on the active load balancer, except for these differences:-
In the
vrrp_instanceblock, change theinterfacevalue to the name of the network interface that receives traffic on the server. -
Change the
statevalue toBACKUP. -
Change the
priorityfield to have a lower number than the active node. The load balancer with the highest priority is promoted to be the active node. For example, if the priority on the active node is 101, then set the backup node’s priority to 100. -
In the
track_interfaceblock, specify the same interface name that is specified in theinterfacefield.
hapee-vrrp.cfgtextvrrp_instance vrrp_1 {interface enp0s8 # Change network interface namestate BACKUP # Change to BACKUPvirtual_router_id 51authentication {auth_type PASSauth_pass 1234}priority 100 # A lower priority value than the primaryvirtual_ipaddress_excluded {192.168.50.10 # Same IP address as on primary}track_interface {enp0s8 weight -2 # Change network interface name}track_script {chk_sshdchk_lb}}hapee-vrrp.cfgtextvrrp_instance vrrp_1 {interface enp0s8 # Change network interface namestate BACKUP # Change to BACKUPvirtual_router_id 51authentication {auth_type PASSauth_pass 1234}priority 100 # A lower priority value than the primaryvirtual_ipaddress_excluded {192.168.50.10 # Same IP address as on primary}track_interface {enp0s8 weight -2 # Change network interface name}track_script {chk_sshdchk_lb}} -
-
Enable and start the
hapee-extras-vrrpservice:nixsudo systemctl unmask hapee-extras-vrrpsudo systemctl enable hapee-extras-vrrpsudo systemctl start hapee-extras-vrrpnixsudo systemctl unmask hapee-extras-vrrpsudo systemctl enable hapee-extras-vrrpsudo systemctl start hapee-extras-vrrp -
Allow the server to bind to the virtual IP address.
Edit the file
/etc/sysctl.confand add thenet.ipv4.ip_nonlocal_bind=1directive. This directive allows the server to accept connections for IP addresses that aren’t bound to any of its interfaces, enabling the use of a floating, virtual IP.sysctl.confininet.ipv4.ip_nonlocal_bind=1sysctl.confininet.ipv4.ip_nonlocal_bind=1 -
Configure your
bindline in the HAProxy Enterprise configuration to use the virtual IP address.haproxyfrontend myfrontendmode httpbind 192.168.50.10:80default_backend web_servershaproxyfrontend myfrontendmode httpbind 192.168.50.10:80default_backend web_servers -
Reboot the server.
Verify the setup Jump to heading
To check that the VRRP service is running, use systemctl status:
nix
nix
outputtext
outputtext
Manual failover Jump to heading
To activate the standby load balancer while simultaneously putting the active load balancer into standby mode:
-
Edit the VRRP configuration
/etc/hapee-extras/hapee-vrrp.cfgon the active load balancer. -
Lower the
priorityvalue to less than the standby load balancer’spriority. This will put the active load balancer into the standby state and simultaneously activate the standby load balancer. For example, change it from 101 to 90. -
Restart the
hapee-extras-vrrpservice.Reverse these actions to restore the original state.
Failover triggers Jump to heading
The following events can trigger a failover:
- The active node lowers its weight below one of the backup nodes due to a failed health check.
- A backup node is reconfigured with a weight larger than the current active node.
- The active node stops emitting its heartbeat packet to the cluster.
VRRP health check scripts Jump to heading
In the VRRP configuration, the vrrp_script blocks define health checks that can trigger a failover. By default, our configuration checks whether the SSH daemon is running and whether HAProxy Enterprise is running. You may want to add more checks.
Consider this block, which checks the status of the SSH daemon every five seconds. If the service isn’t available, the VRRP instance’s weight (its priority) is reduced by 4 points:
hapee-vrrp.cfgtext
hapee-vrrp.cfgtext
The HAProxy Enterprise health check is similar, except if the hapee-lb process is running, it adds 6 points. The reason is, in case one load balancer has SSH working but not hapee-lb, while the other has hapee-lb but not SSH, the one with hapee-lb will become the active node, even though it isn’t manageable remotely.
hapee-vrrp.cfgtext
hapee-vrrp.cfgtext
The following fields define a vrrp_script block:
| Name | Argument type | Description |
|---|---|---|
script |
string | Command to run. Running pkill -0 checks if any process with the given name is running. If it returns 0, the check passes; if it returns 1, the check fails. |
interval |
integer | Interval (in seconds) between two checks. |
weight |
integer | Points to add or remove to instance weight. |
fall |
integer | Number of consecutive negative checks before considered as down. |
rise |
integer | Number of consecutive positive checks before considered as up. |
VRRP instance reference Jump to heading
The following fields define a vrrp_instance block:
| Name | Argument type | Description |
|---|---|---|
vrrp_instance |
string | Describes a new VRRP instance. |
interface |
string | Interface managed by the VRRP module. |
state |
string | State at startup until VRRP priority negotiation completes. Can be either MASTER or BACKUP. |
virtual_router_id |
integer | VRRP instance identifier, which must be common to all nodes of the same cluster. Each cluster must have a unique ID. The value can range from 1 to 255. |
priority |
integer | Weight of local node in this VRRP instance. NOTE This won’t work on cloud provider networks that disable IP multicast. |
virtual_ipaddress |
string | List of virtual IP addresses to add when the state changes to MASTER or remove when it changes to BACKUP. All VRRP nodes in a cluster must own the same IP. NOTE This won’t work on cloud provider networks that disable IP multicast. |
virtual_ipaddress_excluded |
string | The same as virtual_ipaddress, but IPs aren’t announced in the VRRP heartbeat packet, which reduces bandwidth usage when sending packets. |
track_interface |
string | Tracks interface status and updates priority accordingly. |
track_script |
string | Runs the health check scripts and updates priority accordingly. |
Troubleshooting Jump to heading
Does a packet capture reveal that packets are reaching the server, but the VRRP service doesn’t receive them?
- Check if there is a firewall running that may be blocking the packets. See Prerequisites.
Are you using Cisco ACI and experiencing traffic routing back to the failed node after a failover?
- Disable the IP Data-plane Learning option under the VRF and enable GARP-based IP move detection mode. See Prerequisites.
See also Jump to heading
The VRRP module is a wrapper around the Keepalived software. The syntax we use is different, but you may still find the Keepalived documentation useful.
Do you have any suggestions on how we can improve the content of this page?