We use HAProxy Enterprise to assist in the mitigation of Web Attacks against our network of Bank websites. HAProxy has become a critical part of our security posture, and we continue to add/refine the rules used to help secure our sites and network infrastructure.
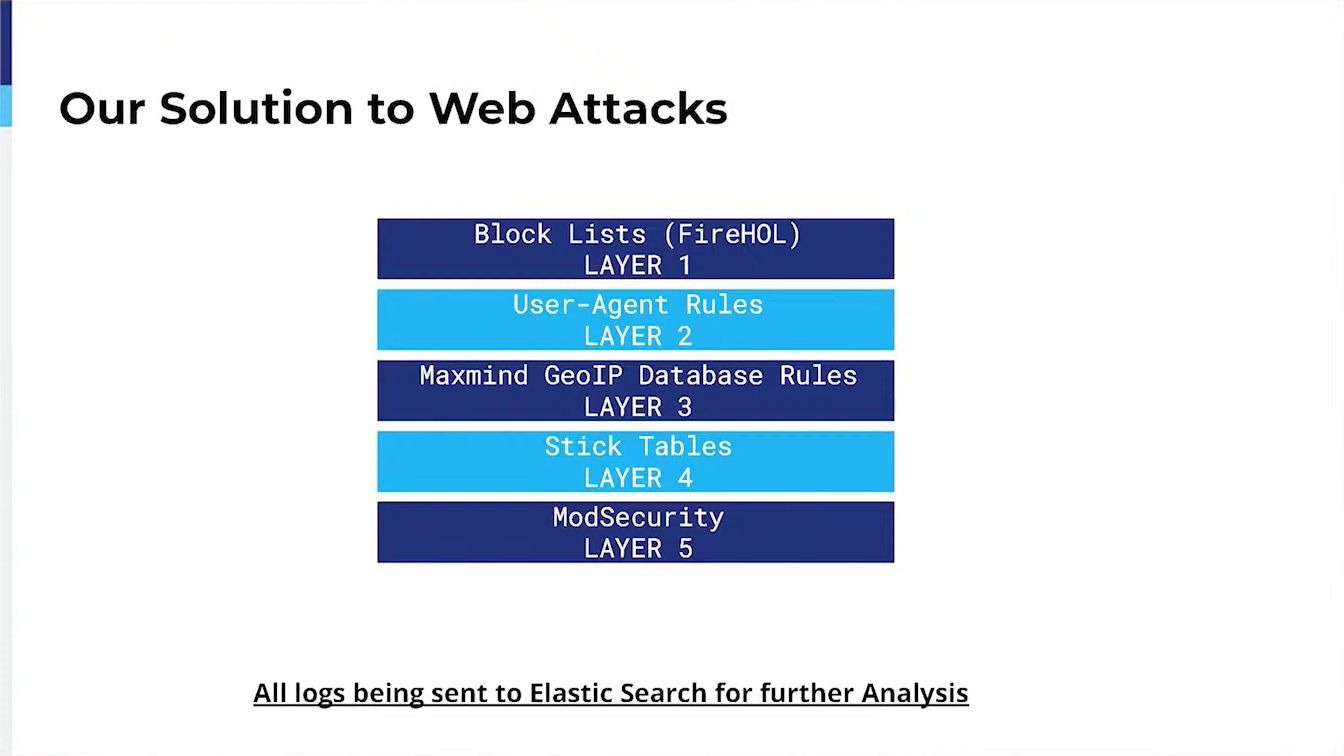
Here at BankSITE, we currently utilize several features from HAProxy Enterprise feature set to help limit their attacks:
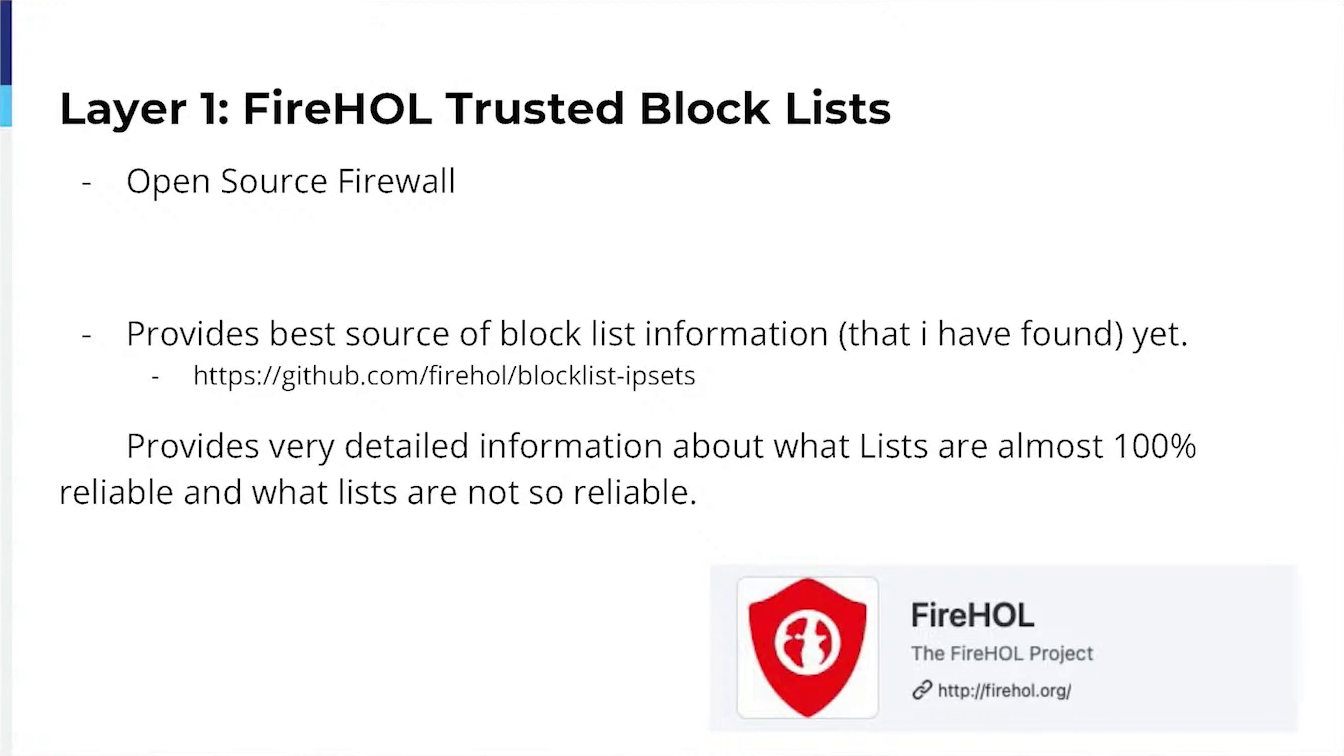
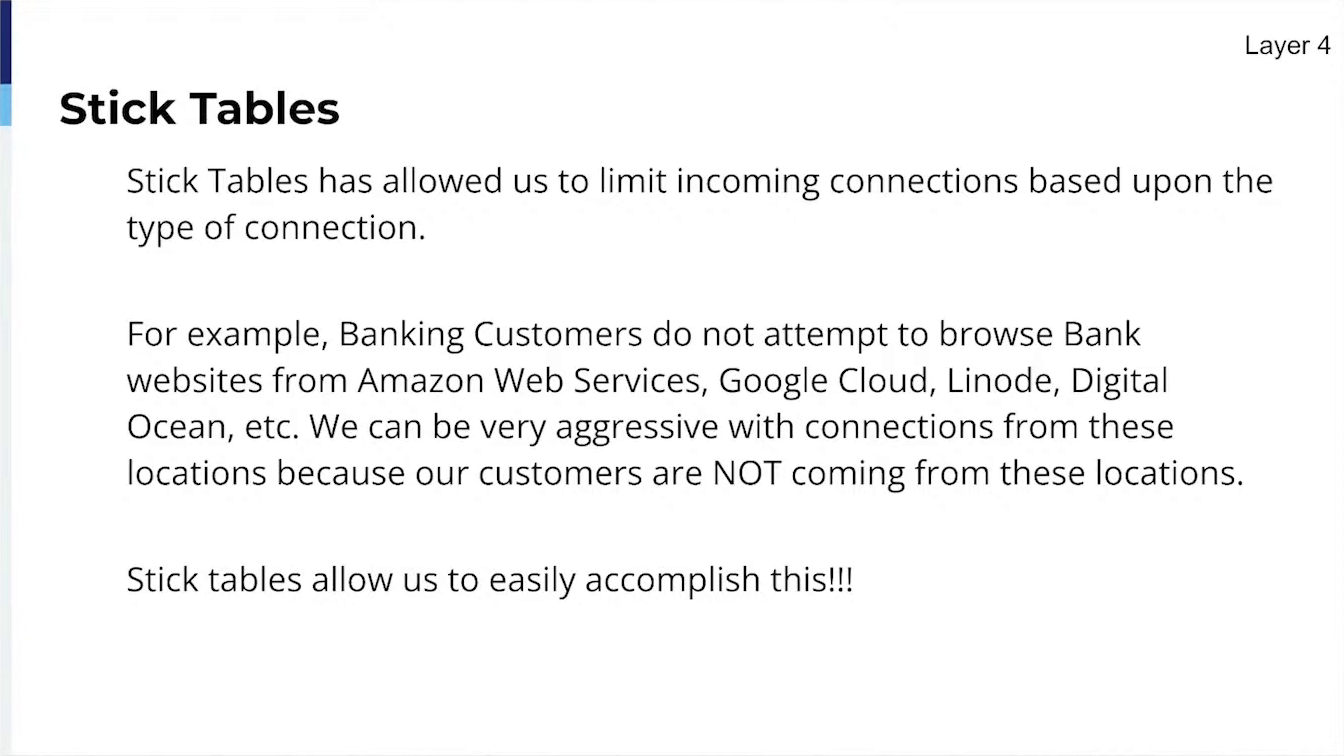
Several Blacklists from Trusted (near zero false positive lists, updated in some cases hourly),
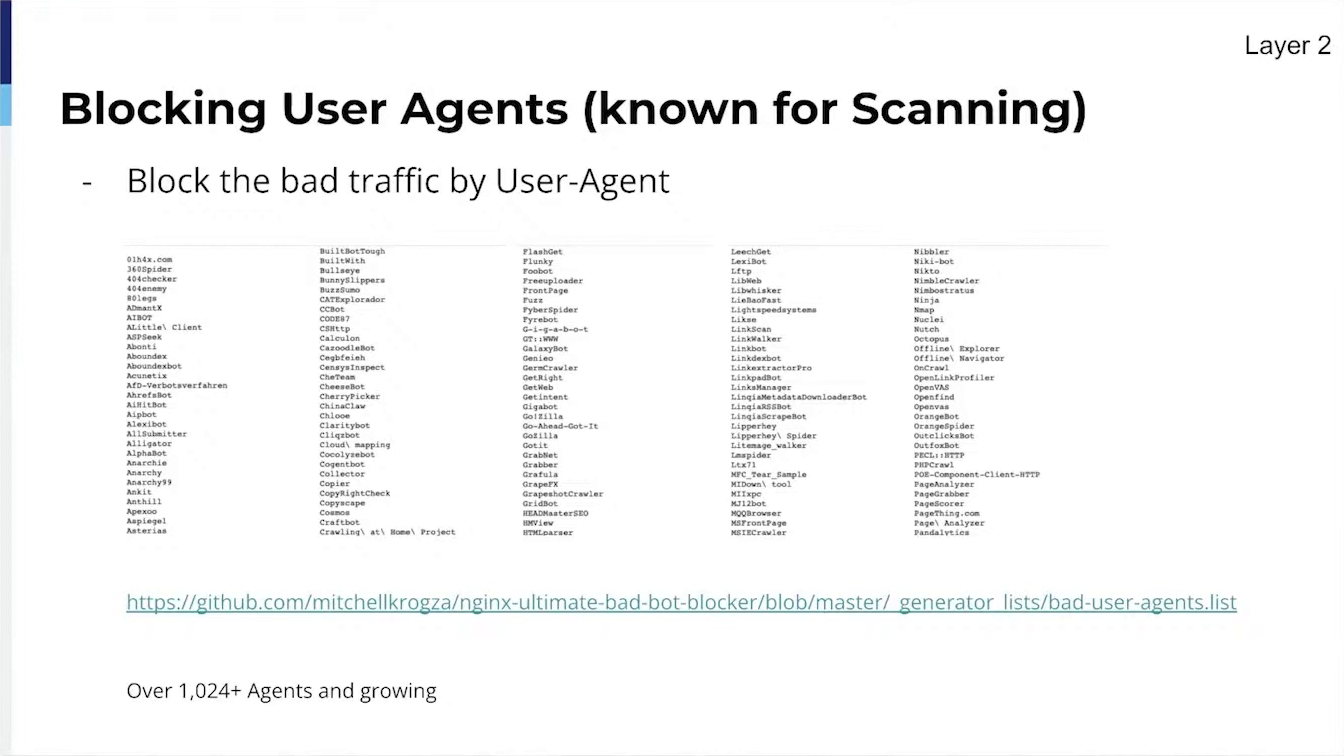
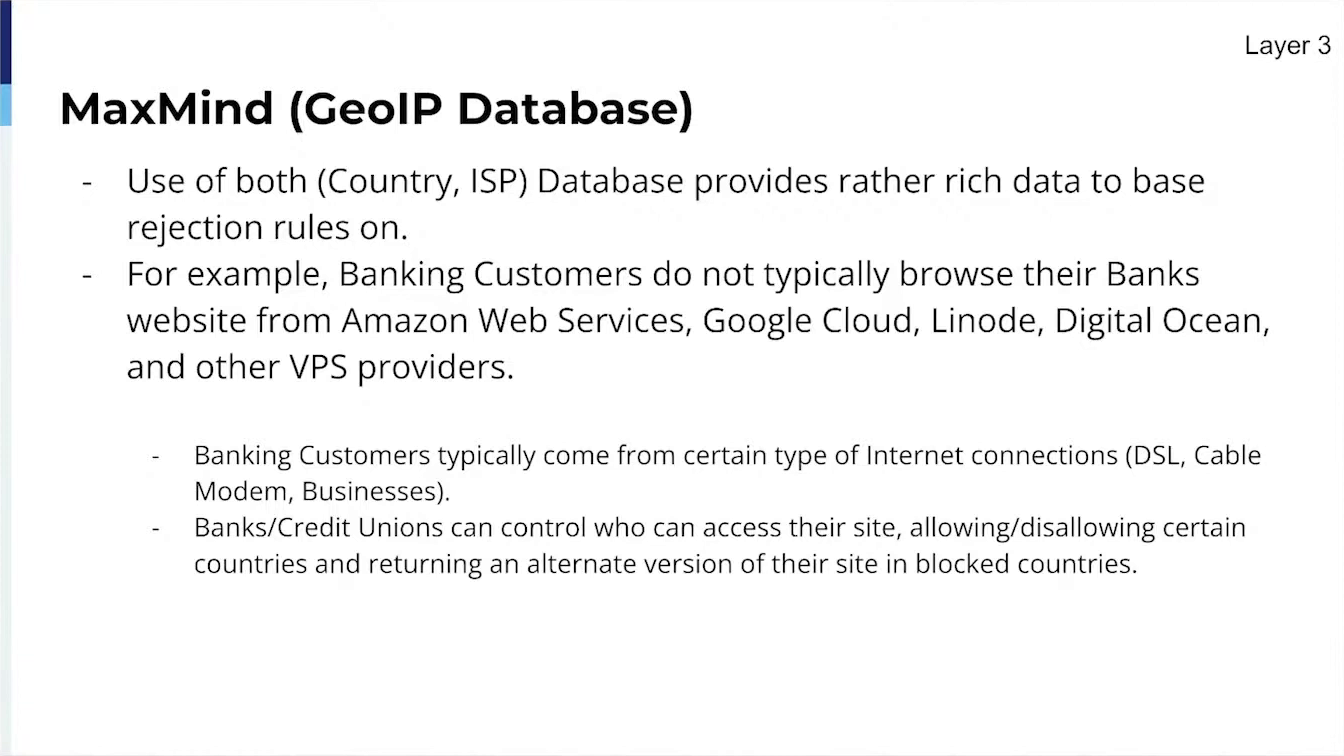
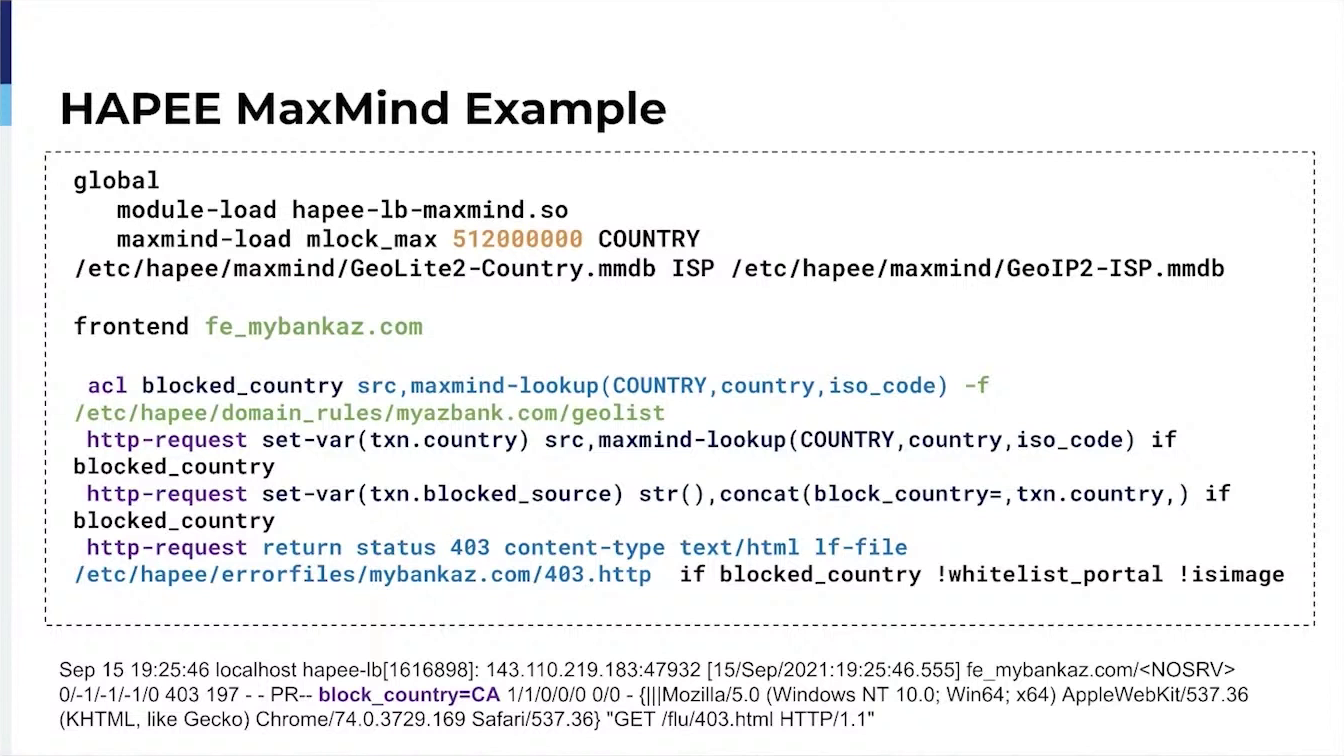
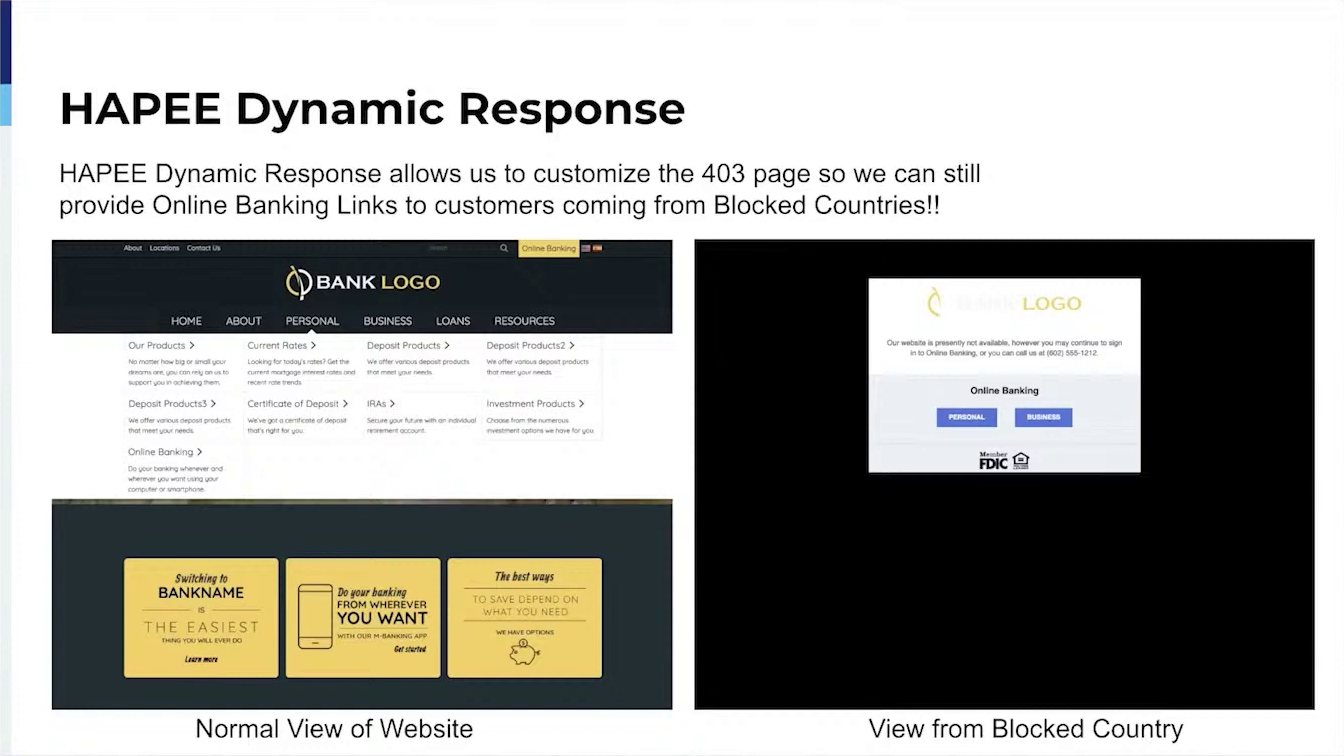
Filtering of allowed Bots, User Agentsy GeoIP (Allowing Customers to select countries that are able to load their full site),
Rate Limiting incoming requests,
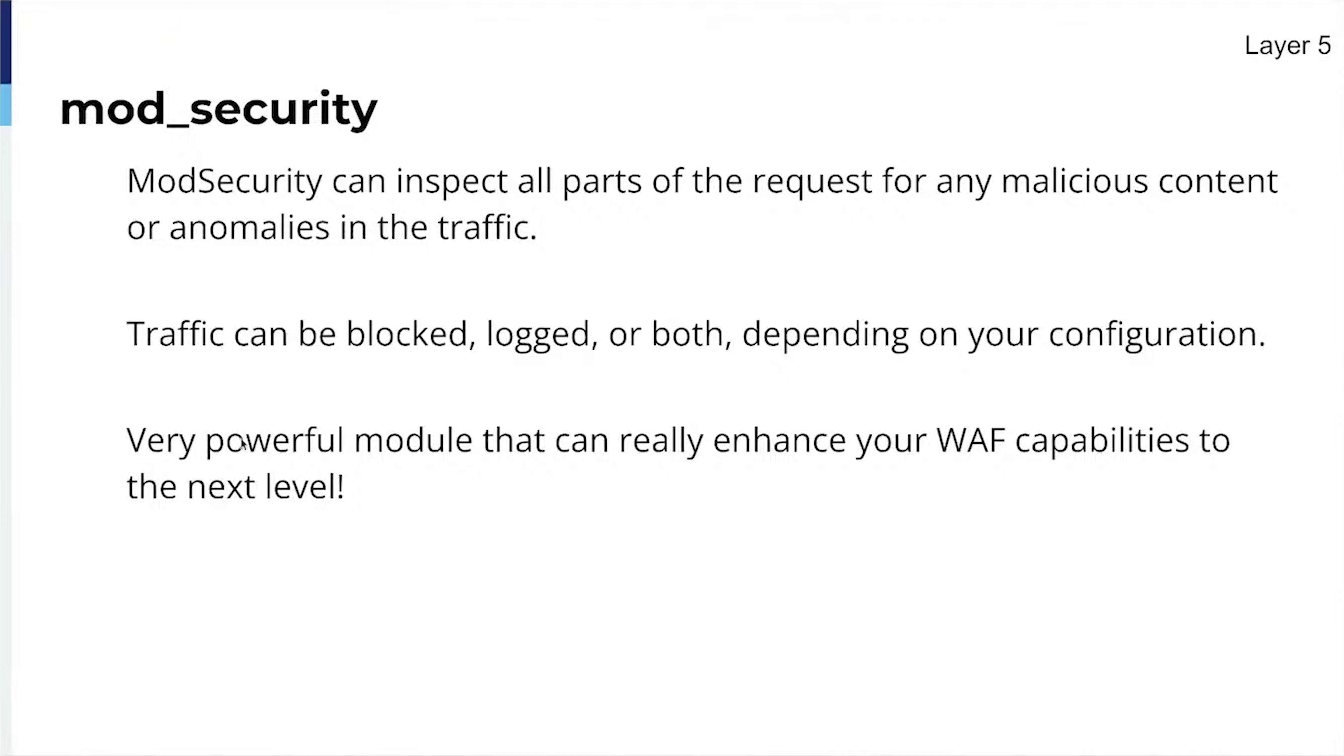
Mod_Security (currently in testing).
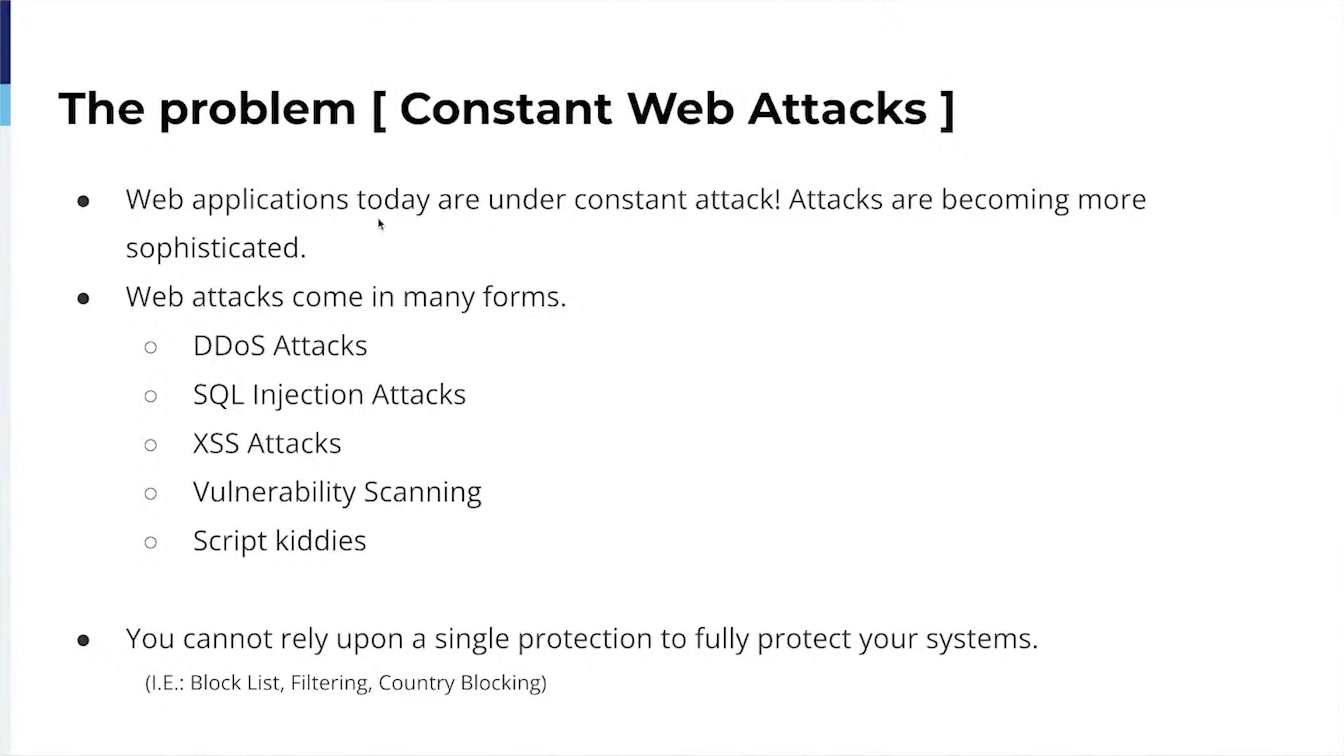
Prior to deploying HAProxy as our primary Load Balancer/WAF, BankSITE’s websites were under constant attack from around the globe. The attacks became some prevalent that it became a daily task of trying to react to the incoming attacks. BankSITE started the hunt to find a product to help us combat the incoming attacks and to bring some sense of sanity to our Network.
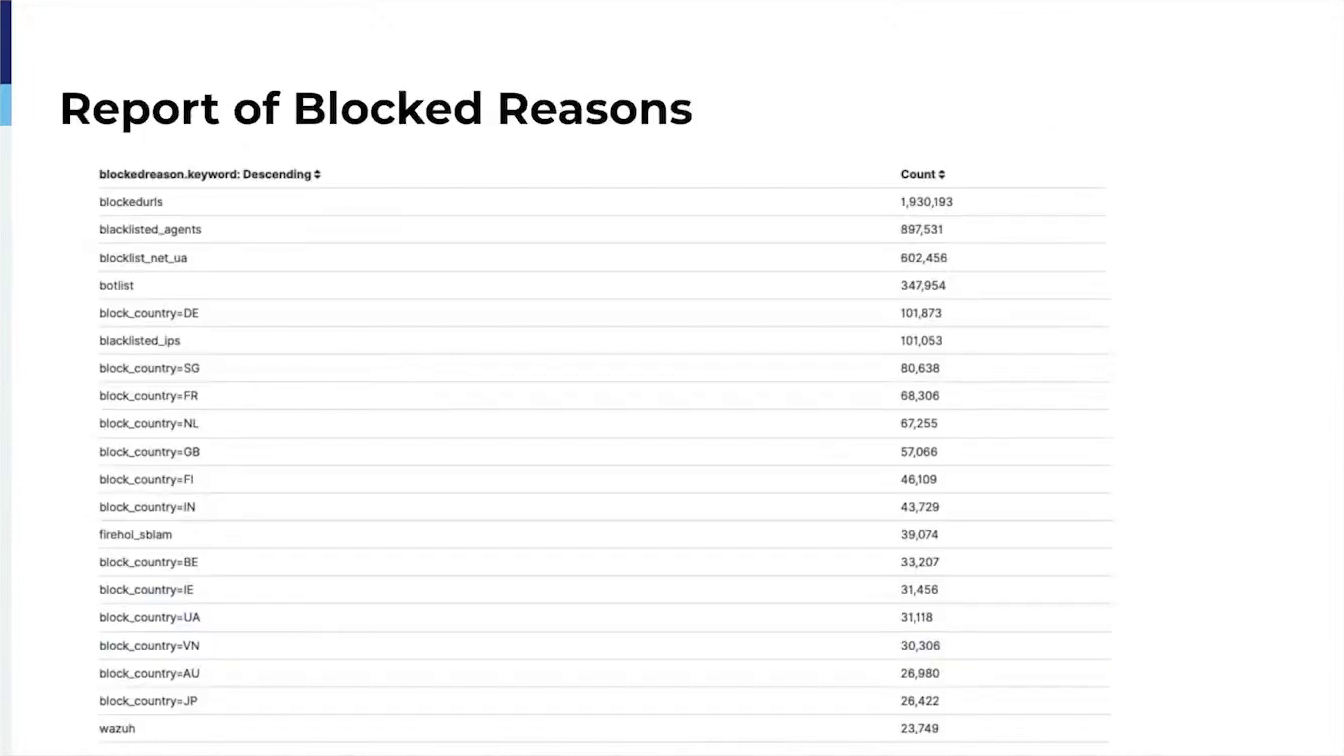
In the beginning, one of our main critical aspects was blocking known attackers. It took me several months to figure out what block lists were semi-reliable and provided almost zero false positives. The talk will provide users with how I found the block lists to trust and how they can also use these lists to block traffic and sleep at night when they aren’t blocking good traffic.
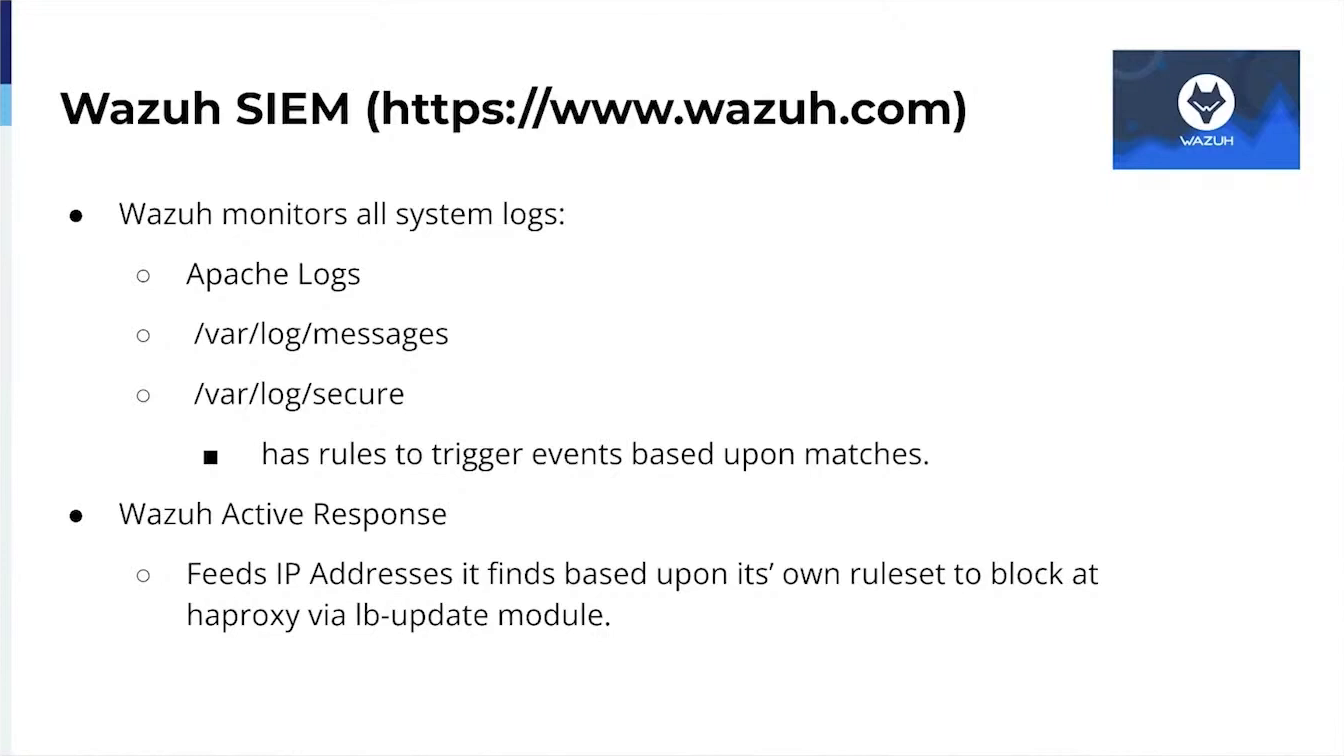
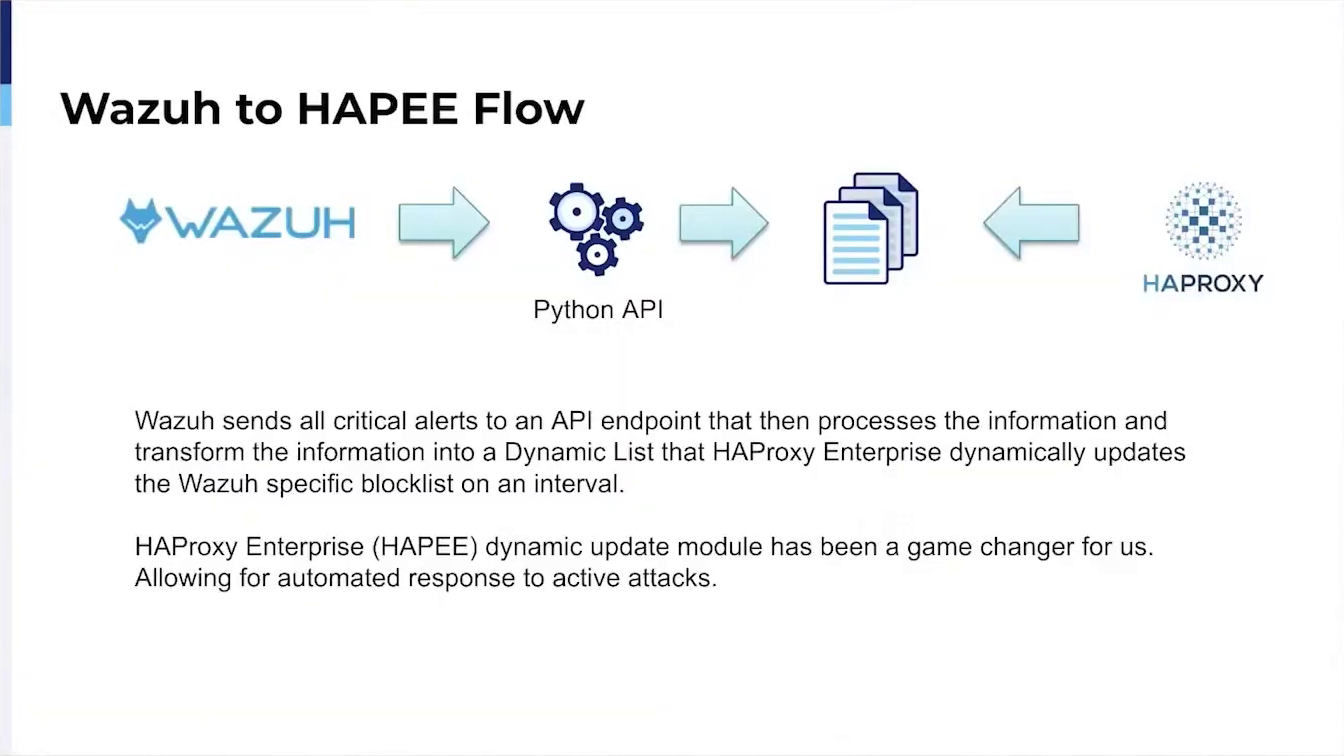
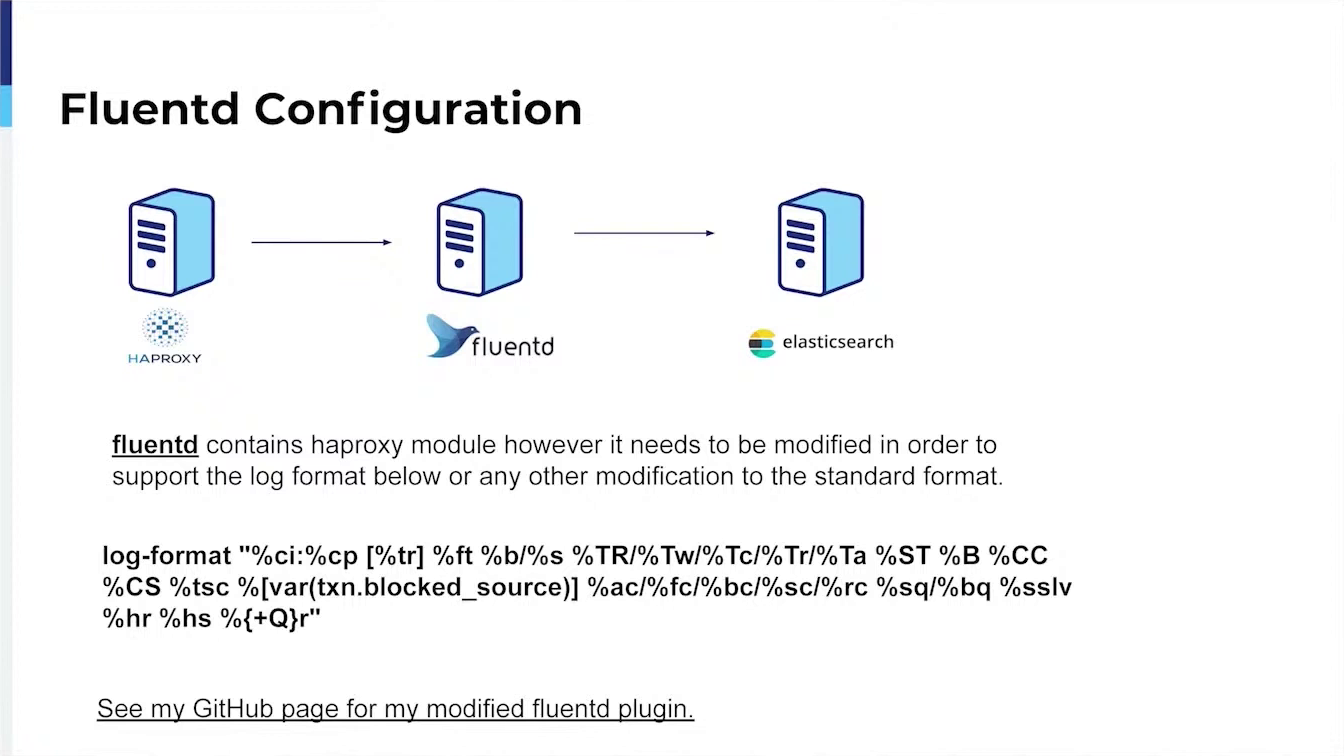
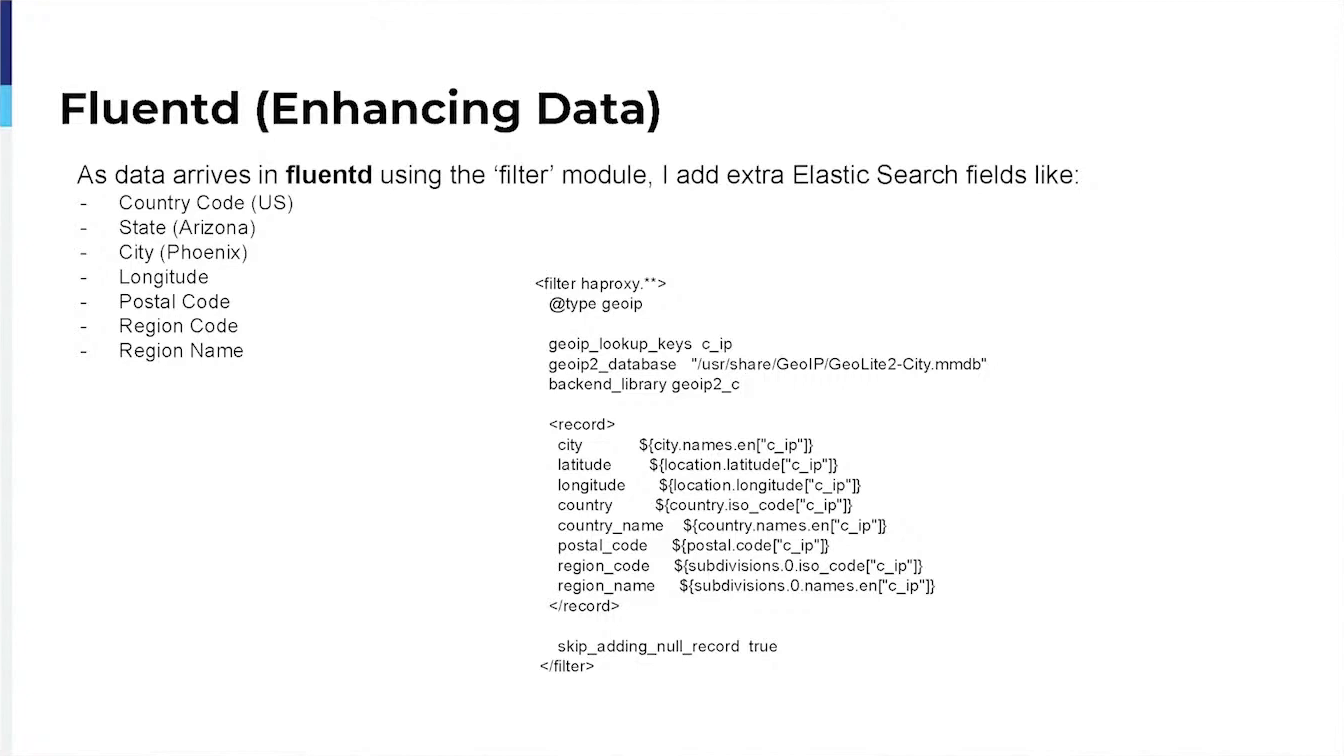
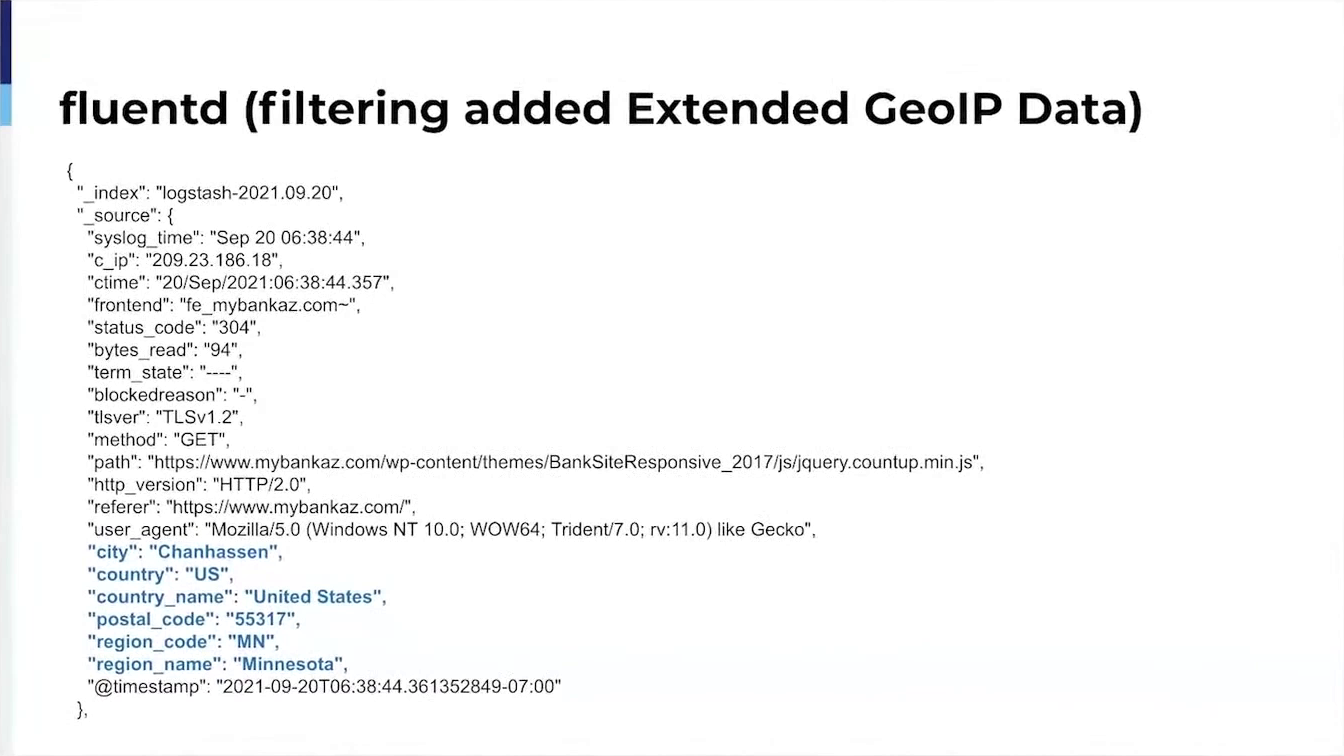
Additionally, I can demonstrate how we digest HAProxy logs into Elastic Search for future analysis and use to generate our own Blacklist of IP addresses not addressed by the bad actors.
Slide Deck
Here you can view the slides used in this presentation if you’d like a quick overview of what was shown during the talk.