Daniel Corbett, Director of Product at HAProxy Technologies, describes recent product changes and unveils the industry’s first end-to-end Application Delivery Platform (ADP), HAProxy One. HAProxy One is designed to simplify and secure modern application architectures and is powered by HAProxy, the world’s fastest and most widely used software load balancer. Featuring a suite of products consisting of application delivery software, appliances and turnkey services managed and observed through a unified control plane, it provides load balancing, application acceleration, CDN, DDoS and bot management, as well as Web Application Firewall capabilities.

Transcript
Hello, everyone. It’s great to see everyone here. Many of us have been communicating for many years over the mailing list, Discourse, IRC, and most recently Slack. We’re really proud to be part of such a great and amazing vibrant community.

At HAProxy Technologies, we truly do love open source and we try to participate with the community in a variety of ways, not only through standard methods such as releasing new open source projects, contributing code to existing projects, publishing high-quality informative blog content, and helping community users over IRC, Slack, and the mailing list as well.
Many of you may wonder how we choose to dedicate engineering resources. We make these decisions after long careful analysis of the application delivery landscape. We gather feedback directly from the community, our customers, our product council, and social media. We continuously track trends and discuss internally which features will benefit the community the most. Sometimes we don’t agree on which features we should implement or which projects we should open source, and for that we’ve implemented a decision support system internally that allows us to come together and make these decisions as a group and not directly within a silo. We also frequently will put out polls to the community asking for your opinion on what features you think we should implement next, or which protocols we should support next.
So we’re always looking to gather feedback and make these decisions for the product. We’re also very interested in hosting meet-ups and attending meet-ups. We think that it’s a great place to bring the community together to talk about our experiences with HAProxy and just in general share our architecture information which each other. Would you like to be a host of a meet-up for HAProxy? Feel free to contact us, hit me up directly if you see me here, and we’ll be more than happy to work with you on arranging that.
Do you love open source as much as we do at HAProxy Technologies? Well, if so, we’re hiring in just about every department within the company. So if you’re interested, again, feel free to reach out from somebody from HAProxy Technologies and we’ll be sure to put you in contact with the right people.

So I’m going to give a brief overview of the last year and recap. In the last year we’ve seen some really exciting changes happen within HAProxy and I understand that Willy has touched on a lot of this, but I’m going to do my best to not repeat. HAProxy 2.0 was released in June of this year and it continued down the path that was started in 1.8, which was the continued goal of supporting the rapidly changing modern architecture.
With the rise of cloud and container platforms, we wanted to make sure that HAProxy could operate within these environments and require minimal configuration to get the best performance. We also began to see a growing need to offer alternative log output options to satisfy container based environments and, for this, we introduced both cloud native threading and cloud native logging.
With the rise of micro services and containers, infrastructures have become more elastic. It’s quite possible that a backend server, quite possibly a Kubernetes pod, disappears while it’s receiving a request, and so for this reason we saw the need to add layer seven retries which will allow HAProxy to either retry that same server or to try a different server if you’re using option re-dispatch. With the release of the Data Plane API, along with the new traffic shadowing or mirroring stream processing offload agent, or SPOA, as well as the community effort to bring polyglot extensibility to HAProxy through SPOE, there was a need to simplify the management of these external components and so a process manager was introduced.
With the new native Prometheus exporter, it now makes it easier to integrate HAProxy into your Kubernetes environment without the reliance on third party daemons or tools and much more. There are so many exciting things in 2.0 and we’re extremely proud of this release and we’re glad it’s been so well received by you, the community.

HAProxy Data Plane API was released. The 1.0 was released in June 2019 in conjunction with the HAProxy 2.0 release. It supports a modern REST API which allows you to dynamically configure and manage HAProxy. It also supports versions and transactions, allowing you to commit either a simple change or several changes at once which must be activated simultaneously. The HAProxy Data Plane API will write to the HAProxy configuration file and also use the Runtime API when possible, which prevents unnecessary reloads. The V2 of the API is coming very soon, so please be on the lookout for that. We have some exciting things planned.

The HAProxy Kubernetes ingress controller was also released in conjunction with the 2.0 release. It was created after a growing need from the community and our customer base to create an ingress controller that HAProxy Technologies could be authoritative on and easily integrate with our HAProxy Enterprise product. It supports TLS offloading, layer seven routing, rate limiting and whitelisting. It also… sorry.

Throughout the last year we’ve also released several other open source tools and components. A major component released is our config native parser which is a Golang SDK which allows you to directly integrate, interact directly with the HAProxy config. Both the Data Plane API and the Kubernetes ingress controller were built using this. Another tool we open sourced was the traffic mirror or traffic shadowing stream processing offload agent, or SPOA. This allows you to copy traffic from your production cluster to another cluster for testing.
Finally, we also released two new Lua scripts in conjunction with some of our blog content. Lua-CORS helps you to easily configure and respond with cross origin access control headers. Lua-JWT allows you to add JWT authorisation and verification to your HAProxy install. We also provided a sample application for integrating with AWS X-ray which is AWS’ version of tracing.
Delivering a Modern Application
So what does it take to deliver a modern application? Traditionally, most sites start in a setup similar to this with an appliance load balancer sitting in front of a cluster of web or application servers. One of the historical advantages to deploying an appliance based load balancer is that they traditionally have purpose-built ASICs for application acceleration, including SSL termination.
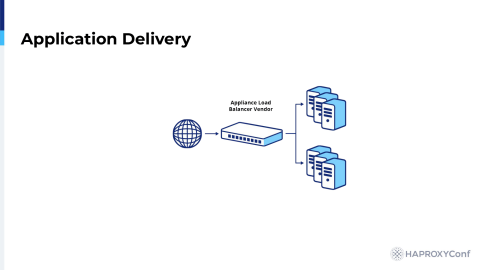
Load balancer vendor
Over time, as your application or your site grows, you find that your site suffers a DDoS attack and so management agrees that there’s a need to purchase a hardware based DDoS protection, so a DDoS mitigation device is purchased and added to the network. The organization sees continuous news coverage about major companies worldwide being hacked. They realize that they don’t really have any protections in place, other than this DDoS mitigation device that they purchased, and so they decide they need to invest in a WAF.

DDoS + WAF + Load Balancer vendors
With the rise of DevOps, we see system engineers and developers wanted to have more control over their load balancers and so they add a software load balancer and extract the advanced routing configuration away from their hardware load balancers. The site’s user base continues to grow over time and global content caching becomes a necessity. The organization brings on a CDN vendor to help alleviate that. After adding the CDN vendor, the organization begins to explore ways to accelerate their application and decide what would ultimately simplify their lives would be to add a turnkey managed application delivery service, such as an ADN, or application delivery network. By doing this, they also gain advanced security features, such as protection against the full spectrum of DDoS attacks, a web application firewall, and bot protection. With application acceleration offloaded, the organization is at a position where they can consider replacing their appliance load balancer.

Adding CDN and ADN vendors
As the site grows, so does the need for a centralized API. The developers argue that it would be much easier for them to manage their applications if they had an API gateway, and so one is deployed within the architecture. As the trend continues, we find developers are now asking for one of their clusters to include a service mesh and be service mesh capable and, before you know it, we’re dealing a lot with a lot of vendors just to deliver our website or application.

Many vendors
One thing I’d like to add that is missing from this is we’re not even showing the ingress controller here, and so before you know it there’s just a wide variety of vendors that we’re dealing with just to deliver our website.
HAProxy One
Application Delivery Simplified
I’d like to introduce to you HAProxy One. It’s application delivery simplified.

HAProxy One is an industry first end-to-end application delivery platform designed to simplify the complexity of modern application environments. HAProxy One unifies the product portfolio which consists of two existing products: HAProxy Enterprise, a high performance software load balancer powered by the legendary HAProxy; HAProxy ALOHA, a hardware and physical appliance and virtual appliance with patented DDoS mitigation technology, Package Shield; and it introduces three new ones. HAProxy Edge which is a new globally distributed application delivery network, or ADN, that provides a wide range of turnkey application delivery services, and HAProxy Enterprise Kubernetes Ingress Controller which is a high performance Kubernetes ingress. It also introduces the HAProxy Fusion Control Plane which will provide a unified control plane. Our Enterprise ingress controller also ships with a web application firewall and we’re the authoritative experts on it as well.
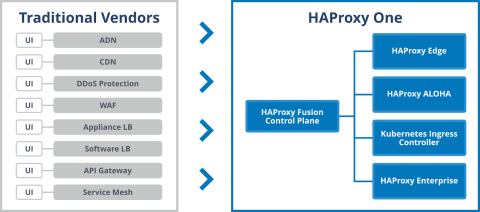
HAProxy One and traditional vendors comparison
So, under active development is the HAProxy Fusion Control Plane which will provide a unified interaction point to the products. HAProxy One consolidates application delivery essentials and allows organizations to unify their architectures.

You may be wondering, why is this important to me in my organization? HAProxy One allows you to simplify the complexity of end-to-end delivery of your application.
With HAProxy at the heart of all of these products, it means you only need to become proficient at one piece of software and apply decades of HAProxy knowledge and experience towards new use cases rather than being forced to integrate diverse vendors and technologies that might reduce performance, reliability, or flexibility. It will also allow you to deal directly with the authoritative experts at HAProxy Technologies. It will feature multi cluster and multi environment support and support role based access control; and it will feature service mesh capabilities in the future.

The HAProxy Fusion Control Plane is currently under active development, as I mentioned, and we’re hoping to offer a preview to customers by Q1 2020. It will also provide, as I mentioned, a unified interaction point. That will be specifically through a REST API, as well as a modern UI. It will provide metrics and alerting.

With the announcement of HAProxy One, we’re also proud to announce a new addition to our product line-up, HAProxy Edge. HAProxy Edge is a global application delivery network which provides protection against the full spectrum of DDoS attacks, a web application firewall, content caching, protection through its CDN capabilities, bot protection, and features first-class observability. HAProxy Edge is 100% architected and supported by the authoritative experts at HAProxy Technologies. We’re currently in 12 locations worldwide and we’re expanding rapidly.

HAProxy Enterprise Kubernetes ingress controller is now available and supports the ModSecurity WAF. It features rate limiting, IP whitelisting, zero downtime config updates, and a built-in stats dashboard.

HAProxy Enterprise 2.0 R1 was just released recently. It contains several backports, such as support for FastCGI, SSL memory enhancements, ring buffer logging, several new fetches and converters, and much more. It also features a hardened ModSecurity implementation which protects ModSecurity from DoS attacks against itself.
We’ve extended support for dynamic updates and now feature dynamic updates for all three supported intelligence vendors: 51Degrees, DeviceAtlas, and ScientiaMobile. With dynamic updates, you’re also able to update ACL files, map files, TLS ticket keys, geolocation databases, and much more. We extended the anti-bot module, which essentially issues a JavaScript challenge to clients who are suspected of having anomalous traffic and essentially it asks the client to prove themselves to be a full-fledged browser. Many of you are already using this today in your HAProxy Enterprise environments and you may be familiar with the standard loading page that you see when this module is triggered. However, we’ve extended this module to add the feature to support templating so that you can customise this with a more user-friendly message.

HAProxy ALOHA 11.0 was released with HAProxy Enterprise 1.9 in April, around April 2019. It is expected for the ALOHA 11.5 to be released near the end of Q4, and we also expect to release a new ALOHA 5300 hardware appliance near the end of Q4 or Q1 2020, sorry.

Booz Allen Hamilton recently implemented a next-generation microservices architecture for recreation.gov as part of the White House’s IT modernisation effort and they provided us with a quote as they’ve been working with us as we built out this HAProxy One platform.

Thank you so much.